A recent survey found that almost all of today’s cars include some form of wireless technology that could be insecure. To make matters worse, most manufacturers may struggle to determine whether or not their vehicles have been hacked. Physical attacks via onboard diagnostic devices have shown that it is possible to manipulate some systems, steering for example, even while cars are moving.
Cybersecurity is, therefore, an increasingly urgent issue for the automotive industry. Systems are becoming more complex, and the threats are becoming more sophisticated. This issue will only get worse as the communication needs of vehicles increase. However, a range of best practices exist, from management focus down to technical measures, which can help to control the risk.
Security
The shift from independent, closed vehicle systems to a connected environment is a huge change for the industry. All vehicle systems must therefore have these three, mutually reinforcing qualities:
- Secure: Prevention is better than a cure, and effective risk management begins by preventing system breaches in the first place
- Vigilant: Hardware and software can degrade, and the nature and type of attacks can change. No level of security is perfect. Security must therefore be monitored to ensure it is still secure or to see if it has been compromised
- Resilient: When a breach occurs, there must be a system in place to limit the damage and re-establish normal operations. The system should also neutralise threats and prevent further spread.
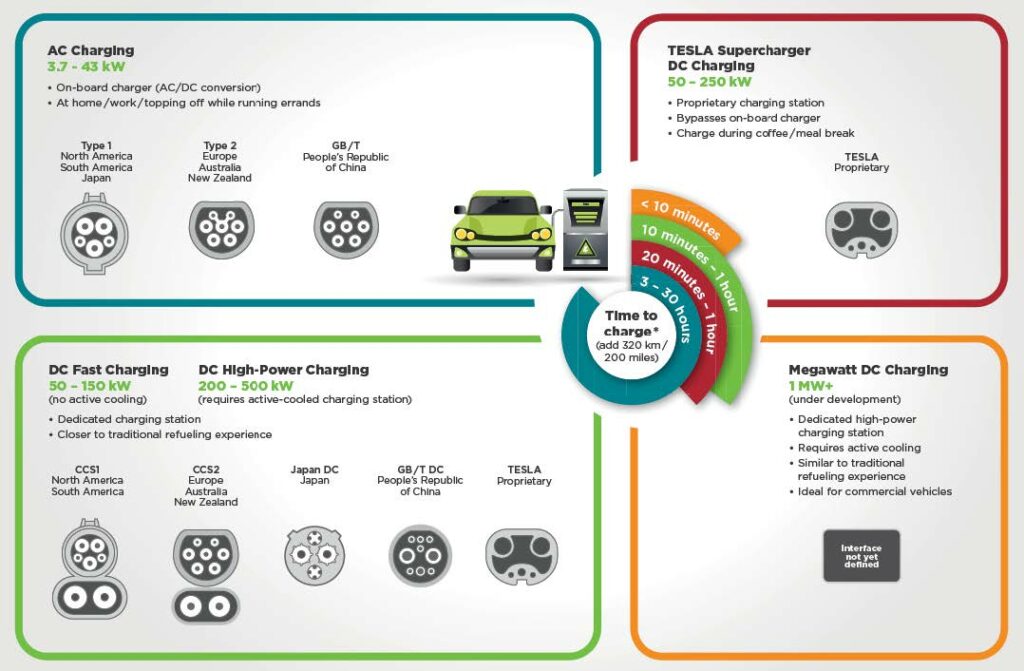
A top-of-the-range car can contain:
- About 150 computational systems running up to 100 million lines of code
- GPS devices that aid navigation and report on real-time traffic
- Diagnostic systems that check maintenance needs and send an alert in the event of an accident or breakdown.
IBM have produced a useful ‘Drive with confidence’ infographic, which is presented here:

Figure 5 Trusted ecosystem (Source: IBM)
Layers of defence
Many layers of defence need to be used on a vehicle, Ford call it ‘Defensive Depth,’ but there is always a balance between ease of access and overall security. One example of a simple security feature (defence) could be that if a vehicle unlock request is received from a phone app, a geographic check could show if the request was local. This is the most likely scenario, but it could be genuine even if from another country, hence the balance required between security and ease of use for the owner.
Summary
Connected vehicles bring many of the benefits of internet access, but they also bring security issues including the threat of dangerous cyberattacks. However, to reduce the chances of a successful attack, from within our businesses, is relatively simple. Follow the five cyber essentials.